To fight the good fight against hackers and other cyber no-goodniks, it’s not enough to just install a cybersecurity system in your manufacturing operations. To adopt the policies that will make those cybersecurity efforts more effective, more cooperation is essential between operations and the IT side of the enterprise. That’s the impetus behind a growing trend with traditionally IT-focused companies working more closely with industrial cybersecurity specialists.
The latest announcement comes today from SCADAfence, which has joined Gigamon’s ecosystem partner program, the two companies working to provide a joint cybersecurity offering. SCADAfence, as the name suggests, was built around the SCADA environments of industrial operations. This provides Gigamon—traditionally strong on the enterprise side of cybersecurity—inroads into the growing industrial market. The deal will enable new business opportunities for SCADAfence, and will help both companies expand into industrial environments driven increasingly by an IT/OT convergence, said Yoni Shohet, SCADAfence’s co-founder and CEO.
Though some companies still face a huge clash between IT and OT departments, Shohet said, he is seeing that, in order to effect change, the teams must be combined. “It has to come together,” he said. “Otherwise, it just doesn’t work.”
This isn’t the first such partnership for SCADAfence, which announced an alliance with Check Point Software Technologies (also focused primarily on enterprise cybersecurity) earlier this year. It’s a trend that’s good for the industrial market, according to Shohet. “There are more IT security giants and main vendors starting to go after the industrial market,” he said. “That’s great news for the industrial security market because more efforts are being focused on raising awareness and improving manufacturing environments.”
The coming together of IT and OT teams is vital for this development. If the decision-making were not becoming increasingly shared by operations and traditional IT functions, there would be no interest from companies like Gigamon and Check Point, Shohet said.
It’s not just a plea made from suppliers to their manufacturing customers; it’s often a cry from manufacturers for help. The deal between SCADAfence and Gigamon, in fact, was prompted by a customer that was using Gigamon on the IT side and SCADAfence on the industrial side, and wanted to see the two solutions come together. “It’s a very large manufacturer with operations worldwide,” Shohet described. “One of their biggest challenges is that they have dozens of facilities worldwide. They need to have an efficient way to monitor all these activities.”
And it’s a need that SCADAfence is hearing from more of its customers. The company serves primarily the smart manufacturing space, including pharmaceutical, chemical, food and beverage, and automotive manufacturing. These are industries that face multiple cybersecurity concerns that aren’t so prevalent in other industries.
Although a lot of public concern has been focused on the cyber threat to critical infrastructures and utilities related to energy and water supply, critical manufacturing industries actually figure more prominently in cyber attacks. According to investigations from the U.S. Department of Homeland Security, cyber attacks on U.S. critical manufacturers nearly doubled last fiscal year to 97 reported incidents. That compares with 46 incidents for energy, 25 for water, and 23 for transportation systems.
And while infrastructure-related operations like energy and water are primarily concerned about operational downtime, manufacturing environments add to that concerns about product manipulation and theft of intellectual property. Shohet made reference to a case a few months ago in which Mars had to recall chocolate bars across 55 countries after a red piece of plastic showed up in a Snickers bar in Germany that had been made at a factory in the Netherlands.
That was not cybersecurity-related, but rather an operational error, Shohet said. “But if they can’t find these types of errors, how are they going to find it when somebody tries to hide these manipulations?” he asked. “This is the kind of damage that can happen to revenue and reputation. This won’t be the target of an attack to an electrical company.”
Other examples of cybersecurity concerns in critical manufacturing relate to sensitive data that adversaries could try to target for financial damage. “The machines know everything about proprietary methods used by a company,” Shohet noted.
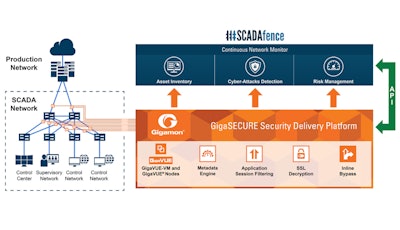
The joint offering announced today leverages Gigamon’s capability to provide visibility of network traffic from across the ICS/SCADA environment, ensuring continuous traffic monitoring. The network traffic is passively gathered by Gigamon, deduplicated, aggregated into scalable traffic streams and then passed to SCADAfence’s continuous monitoring solution, which analyzes the internal communications, including industrial protocols deep packet inspection (DPI).
SCADAfence’s Industrial Continuous Network Monitor system is fully interoperable with Gigamon’s GigaSECURE to provide IT and OT security personnel with a holistic view of their industrial network, as well as advanced detection capabilities. The joint solution restores control of the industrial environment and mitigates risks.





















